How i got idor with xss ;)
Hii everyone today i’ll share the simple bug that i found in July 2019 that allowed me to change user’s First and Last name remotely in Emsisoft main domain. so without wasting more time let’s begin. This is my first ever writeup so there might be some mistakes so please ignore it. :
In July i was testing the Emsisoft.com main domain. after testing a few funtionalities i got some low hanging bugs like no rate limit, ssrf to xspa and few issues which went to be duplicate although Emsisoft is filled with many duplicates.. i was sure i won’t get anything but as the saying goes where there is a will there is a way…I didn’t give up… I kept digging….
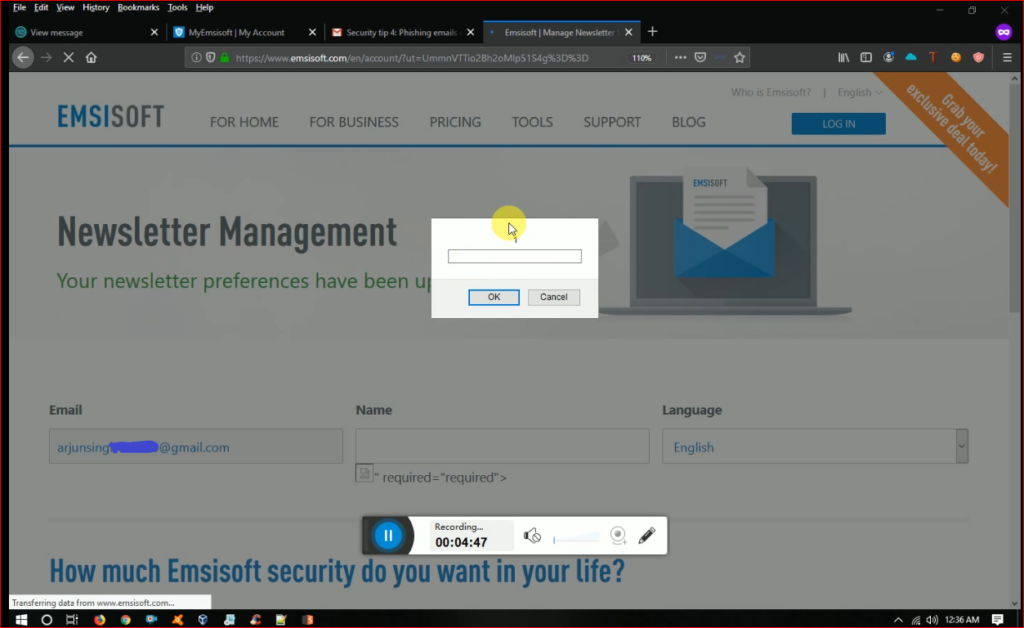
After a few days i was checking my secondary email i got newsletter from Emsisoft i was fed-up with their emails as it was spam for me. I was about to unsubscribe the email. as soon as i click on unsubscribe link i got this dashboard
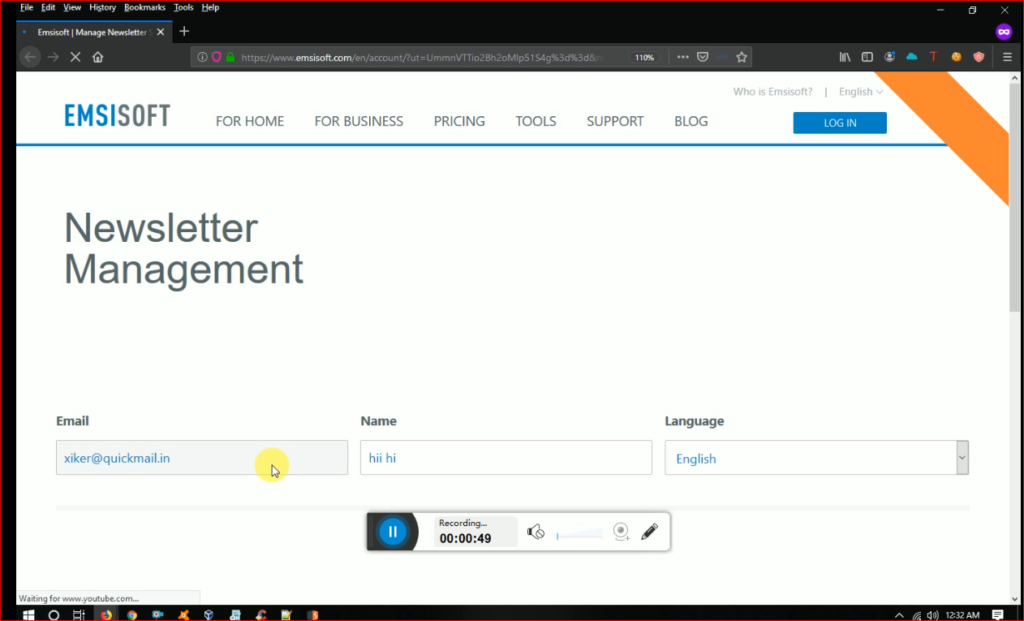
Now i saw that the email field is disabled, we can’t edit email but the name field is enabled that means we can type name and this was vulnerable for xss . I submit the Request with appropriate manner and intercept the request with burpsuite i got this
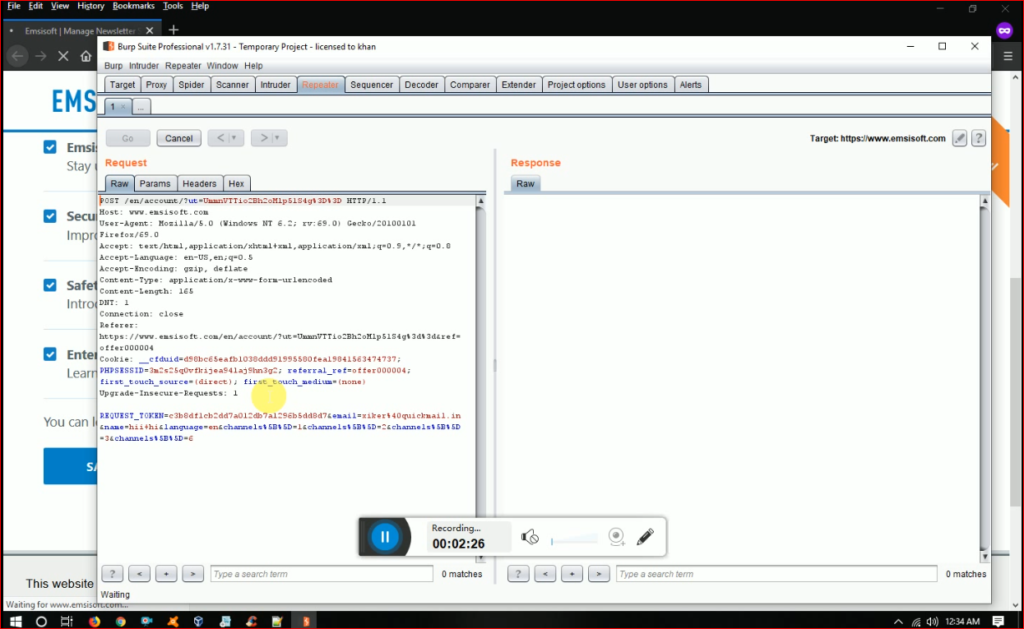
Now i guess you may have clear idea what i am going to do here. i change the email with my 2nd account and in name field i typed different name payload in order to recognize properly
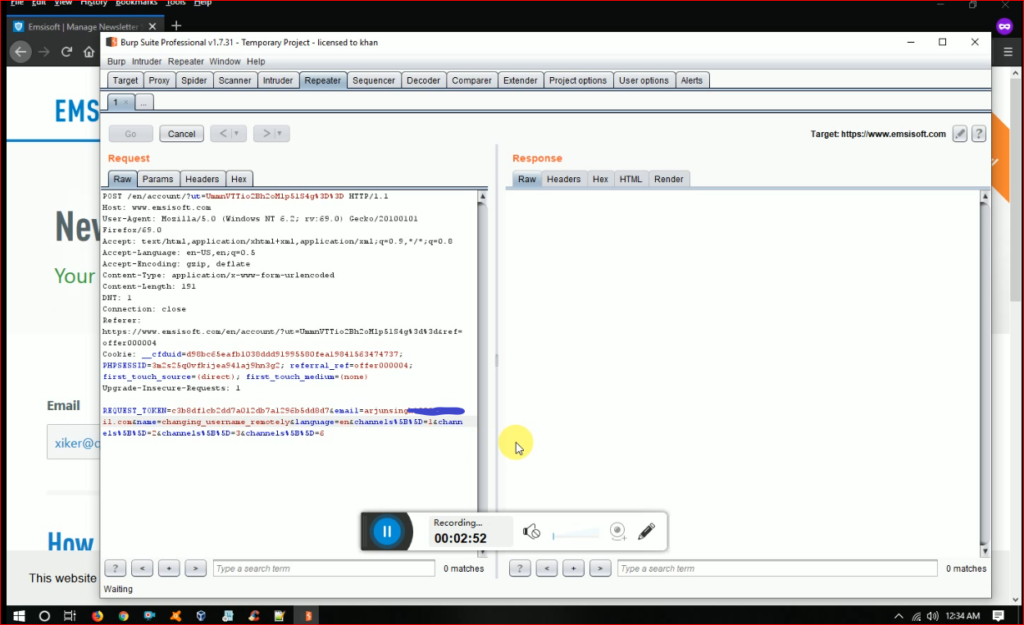
Now i forwarded the request to server and i check the my 2nd account and my 2nd account’s name was changed

Now it was time to try stored xss. i immedietely change the name field with xss payload and forwarded the request But it was not firing on myprofile . but on visiting unsubscribe link
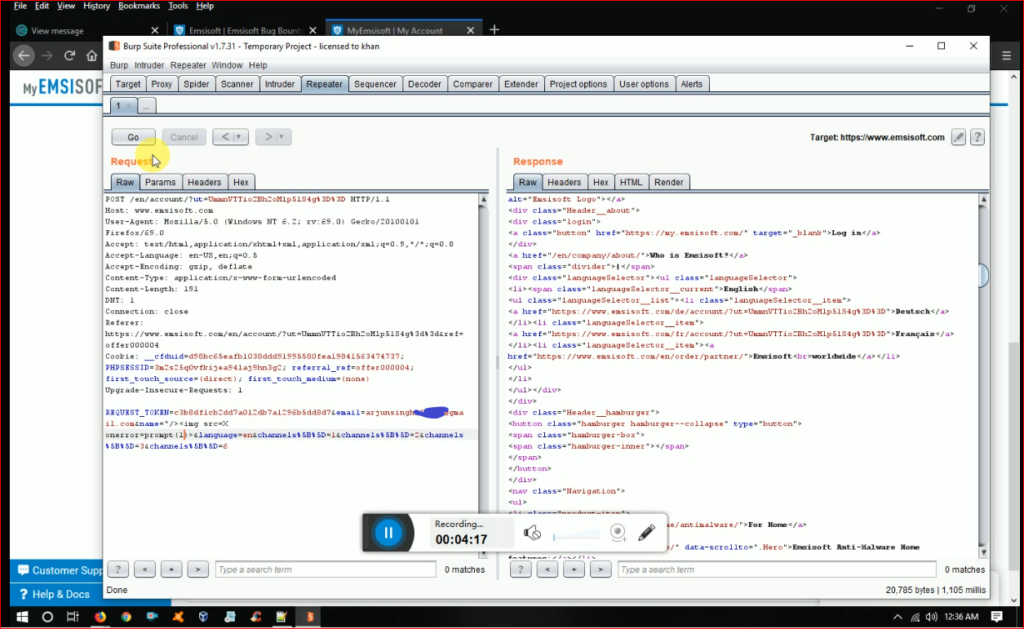
Scenario was like if arjunsinghxxx visit the unsubcribe link then xss payload will fire thus it was on name field
They awarded me 100$ because company’s budget was a bit low.
Takeaway:
Always check each and every functionality of the target. There’s always a chance. Never lose hope. Even a small think could make a big difference..
As you can see the payload which i used was very basic. This tells that there’s always a chance. Never lose hope. Keep Digging. You’ll definitely get something…. Happy Hacking 😉
I hope you enjoyed reading..!!
Hi All! I Arjun Singh, Synack Red Teamer and Independent Security Researcher , specializing in web application and API’
Currently, I am working as a security analyst at payatu, where I am part of the Security Consulting team at Web Security Testing as well as we perform the Secure Code Review as well



Keep up the good work and like your blog very much my friend
Looking forward for more blog and epic bug finiding with you all the best for your future and future work keep grinding looking forward for more
😎😎😎😎😎
Thanks For Your Response Share it with your friend too 🙂
Very great post. I just stumbled upon your blog and wished to say that I have truly loved surfing around your weblog posts.
After all I will be subscribing in your feed and I am hoping you write again very soon!
Sure i will write more blogs